Built To Defend Against Tomorrow’s Threats Today
Protect a device connected to a network from malware, malicious applications
and investigate security incidents and alerts.
The World's Most Secure Operating System
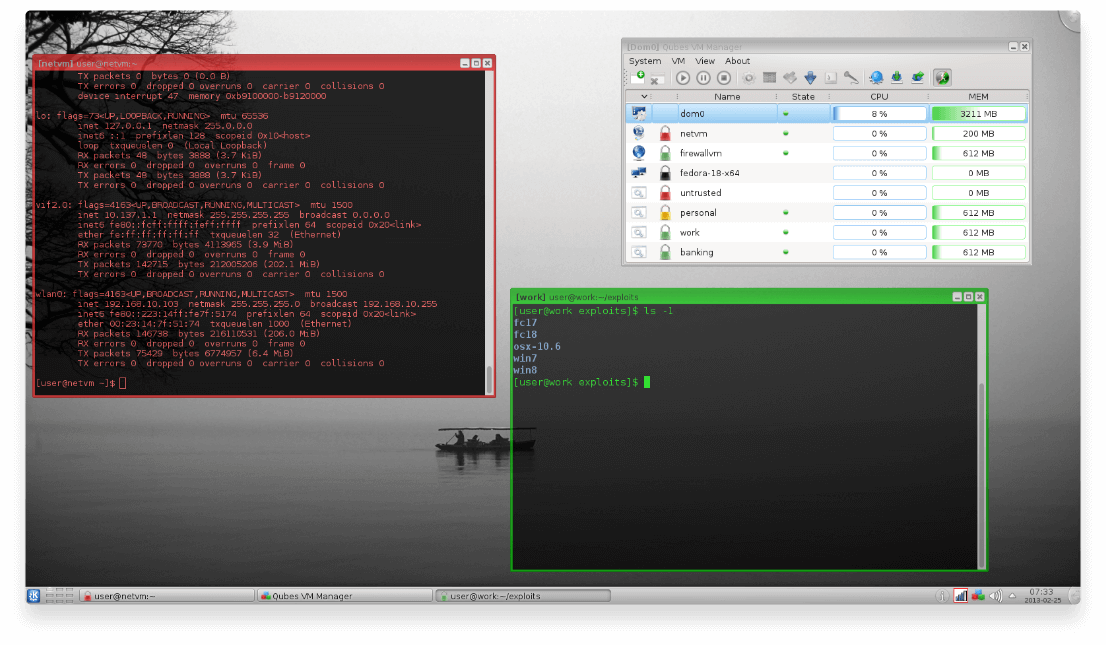
Isolate software as if they were installed on separate physical machines using PV or HVM virtualization techniques.
Allow qubes called AppVMs to share a root file system without sacrificing security using the innovative Template system.
Use multiple operating systems at the same time, including Fedora, Debian, or Windows.
Create disposable VMs which are spawned quickly and destroyed when closed.
Run Tor securely system-wide using Whonix with Qubes.
Secure device handling through isolation of network cards and USB controllers.
Utilize Split GPG to store private GPG keys in an AppVM.
Operate Qubes U2F proxy to use two-factor authentication.
Users are free to use, copy and modify Qubes OS and are encouraged to do so.
Open Source Secure Firmware
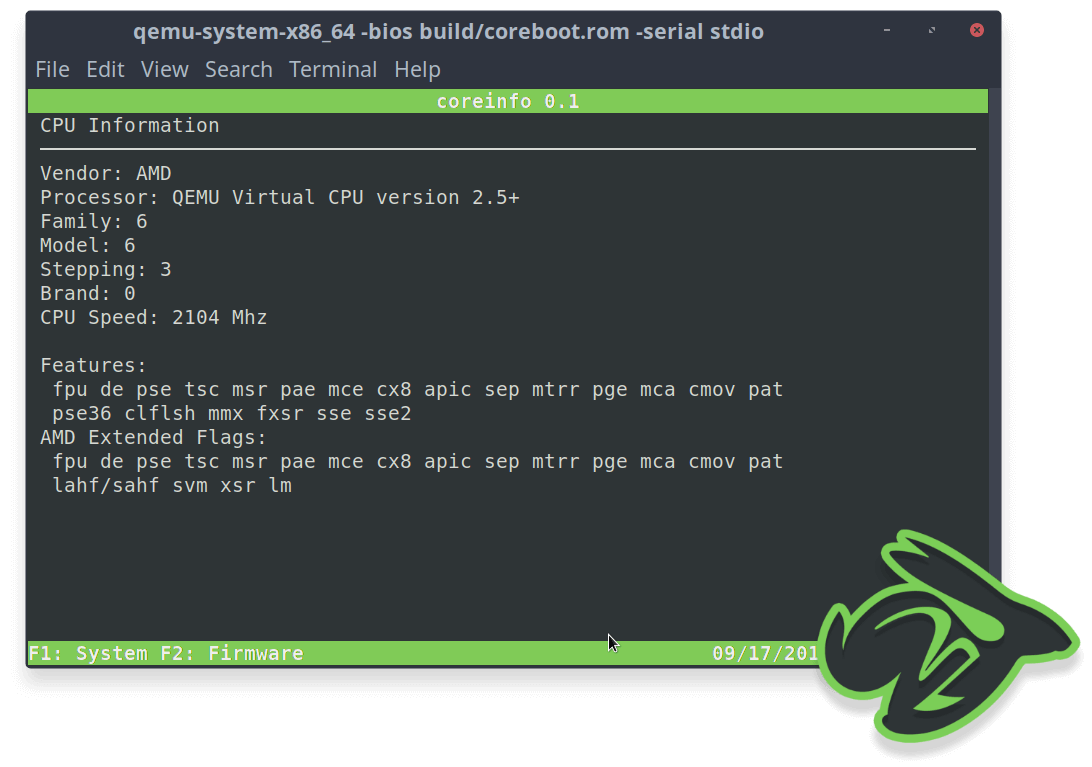
The primary flexibility that coreboot offers is through the use of different payloads. We support legacy OS boot through SeaBIOS, network boot with an integrated iPXE ROM, or the latest UEFI payload. Customized payloads can be created using the BSD licensed libpayload toolkit.
Coreboot comes with a minimal Trusted Computing Base which reduces the general attack surface. It also supports a secure boot process called VBOOT2. It’s written in MISRA-C standard and provides other languages like Ada for formal verification of special properties. Also the use of platform features like IOMMU, flash protections and deactivated SMM mode increases the security as well.
The architecture of coreboot is designed to have an unbrickable update process. Updating firmware should be no more dangerous than installing your favorite app on your mobile phone.
Coreboot is designed to boot quickly. For desktops and laptop machines, it can frequently boot to the start of the operating system in under a second. For servers, it can cut minutes off of the boot time. Some vendors have demonstrated a decrease in boot time by more than 70% when compared to the OEM BIOS.
Keep Your Employees Safe and Productive
Use the power of AI to offer protection from malware, hackers, viruses, ransomware and malicious websites.
Traditional Antivirus typically uses a signature based model, which is reliant on capturing new viruses in the wild and creating a master list of malware for users to download. This makes it especially vulnerable to zero-day attacks and modern threats which can alter themselves too quickly for signature updates to catch.
Traditional antivirus waits for you to be infected before it can act. Cylance observes the behaviour of programs in real-time, detecting threats in milliseconds - before they can execute.
Proactive AI provides protection from all types of malware, existing threats and those yet to be developed.
Cylance prevents attacks before they happen rather than relying on other users becoming infected to 'discover'.
We know you just want your antivirus to keep you safe, not waste your time. That’s why we guarantee to never bother you with unwanted alerts or pop-up ads. Promise.
We do all the computational heavy lifting in the cloud. As a result, Cylance uses much less RAM and CPU than other AV solutions, making it perfect for gamers or alongside other intensive processes. You won't even notice we're there.
Solve your password management problems
Your online safety is at risk
Password theft is a serious problem. Your online accounts are consistently under attack which is why
strong password security practices have never been more critical.
Lock your passwords and private information with end-to-end AES-256 bit encryption, salted hashing, and PBKDF2 SHA-256.
Secure and share sensitive data within your Bitwarden Vault from any browser, mobile device, or desktop application.
Share your encrypted data quickly and easily, and only with the users or teams who need access.
Open source and third-party audited, Bitwarden complies with Privacy Shield, GDPR, CCPA regulations.
Access insightful reports to reveal weak, reused passwords, and other helpful data security metrics.
Our powerful Directory Connector streamlines user and group onboarding and keeps them in sync.
Bitwarden creates audit trails to help you keep track of user and group access to sensitive data.
Use our powerful APIs to automate onboarding and management functions.